Secure your ERP like a control room-access, approvals and audit trail built-in.
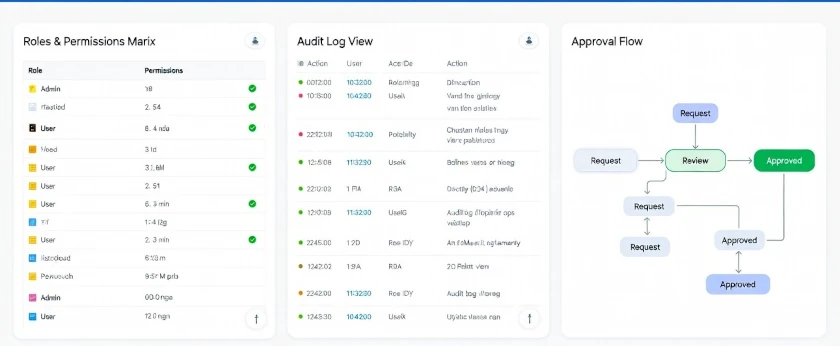
Most data leaks and business losses are not “hack” stories-they are internal mistakes, uncontrolled edits, or unauthorized access. Webhuk ERP Security gives you practical controls: role-based access, permissions, approval checkpoints and audit logs so your team works fast without compromising governance.